Demo Wifi AP sniffer
-
Since it offers a really easy (I mean, really really easy) way to configure it as wifi access point, my first project was try to run a traffic sniffer / inspector — technically, I need to use it to demostrate how using free wifi is insecure (MITM kind attacks). Basically, we will run tcpdump on the Omega2+ and read the captured traffic remotely with Wireshark.
The Omega2+ runs a particular branch of OpenWRT called LEDE. This can make things quite complicated sometimes but not this time.
First, plug-in the Omega2+ and do all those sweet steps that the setup prescribes. Once done, activate the AP functionality from the web interface. Just one click.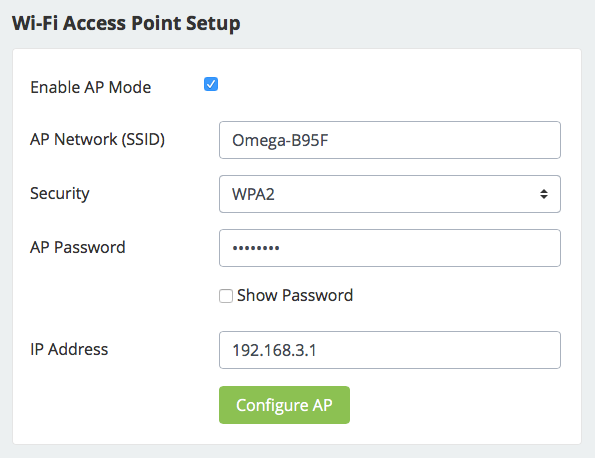
Now, every computer connected to the Omega2+ wifi will be able to use the Internet and all traffic will be bridged between the two virtual interfaces of the Omega2+. It smells MITM everywhere. So, let’s move on.
In order to install some software to sniff packets, we should re-add the official LEDE repositories: by default, just Onion packages would be active. So:vi /etc/opkg/distfeeds.conf
In the editor, re-enable the LEDE repos and comment out the Onion ones so that you end up with i file like this:
src/gz reboot_core http://downloads.lede-project.org/snapshots/targets/ramips/mt7688/packages
src/gz reboot_base http://downloads.lede-project.org/snapshots/packages/mipsel_24kc/base
#src/gz reboot_onion http://repo.onion.io/omega2/packagessrc/gz reboot_luci http://downloads.lede-project.org/snapshots/packages/mipsel_24kc/luci
src/gz reboot_packages http://downloads.lede-project.org/snapshots/packages/mipsel_24kc/packages
src/gz reboot_routing http://downloads.lede-project.org/snapshots/packages/mipsel_24kc/routing
src/gz reboot_telephony http://downloads.lede-project.org/snapshots/packages/mipsel_24kc/telephony
#src/gz omega2_core http://repo.onion.io/omega2/packages/core
#src/gz omega2_base http://repo.onion.io/omega2/packages/base
#src/gz omega2_packages http://repo.onion.io/omega2/packages/packages
src/gz omega2_onion http://repo.onion.io/omega2/packages/onionReboot the Omega2+ and update package list:
opkg update
If you get an error about the verification of the signature, you need to disable it (this is an issue just because the firmware is compiled by Onion so this verification is not going well). Open the opkg configuration file:
vi /etc/opkg.conf
and comment out the line of the verification of the signature. Try again updating the package list, it should work. We can now install tcpdump, that is the software we are going to use to sniff the traffic (but you already know that). Easy as 1 2 3:
opkg install tcpdump
Incredibly, it’s done. Nothing more needed, YAY!
Now, we’re going to create a pipe on our OSX/Linux system that will receive the data capture via an SSH connection from the Omega2+ (supposed that we still are in the same wifi network) and open Wireshark. On our pc:mkfifo /tmp/remote
wireshark -k -i /tmp/remoteThis will create the pipe and open a Wireshark instance with the pipe as input. Then, in an other terminal window we’ll start tcpdump via ssh:
ssh root@192.168.3.1 "tcpdump -s 0 -U -n -w - -i br-wlan not port 22" > /tmp/remote
Of course, if you changed Omega2+ configuration you will need to change IP address. We also added “not port 22” filter to take out our ssh connection out of the capture: you can add here whatever filter you want.
Immediately, you will see the Wireshark window populated with all the traffic going through the Omega2+.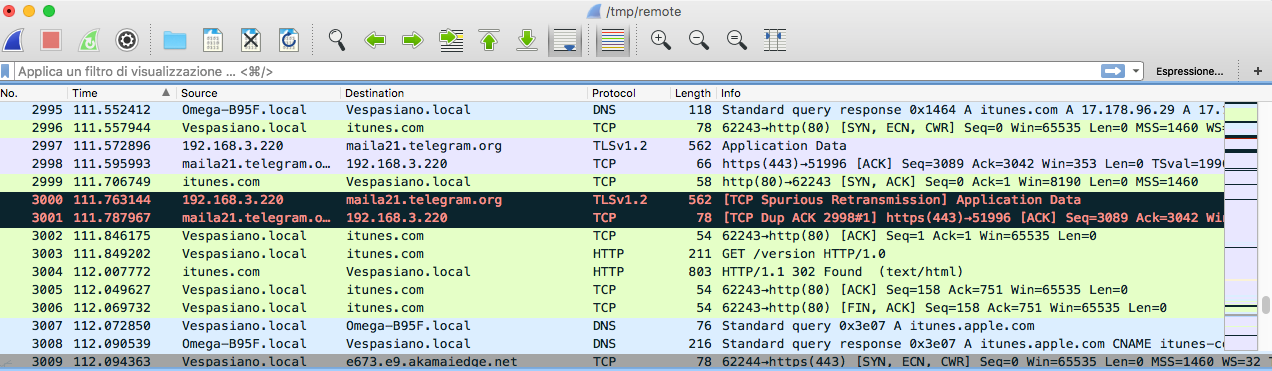
Unfortunately, the type of distro the runs on Omega2+ doesn’t allow to run all that out-of-the-box software to carry a proper and effective MITM attack: anyway, the purpose of my project was to demonstrate to an audience that with a small device powered with a battery pack (so 100% portable) can be used in a public place to steal any kind of data. Another option is to expand the internal memory of the Omega2+ and save the traffic dump in a file that could be later analyzed with Wireshark.
-
@tommaso-tani Will this work with the Omega
-
Take a look at the last paragraph...
-
@Guest you mean with the first version?
-
Awesome Project! Thanks for sharing. I wonder how easy it would be to turn this into a device like an Ekhau wifi heat mapper? Or at least capture and correlate gps data into the stream. Is this device capable of parsing out channel and signal strength from multiple wifi channels simultaneously or by hopping? Is it capable of monitor mode or promiscuous mode?
-
@Hank-Hill said in Demo Wifi AP sniffer:
Ekhau
As far I as know, there have been many problems (read: impossible) to set the Omega in monitor mode - see this post.
I didn't try yet but I think that with the GPS expansion it could be possible releasing something like that..